What is ClickFix? ClickFix is a social engineering technique increasingly being used by actors in the past few months. The technique relies on fooling users to run PowerShell or Terminal commands on their computers, through the use of fake error dialogue boxes. This post will look at how the domains involved in ClickFix script can be latched onto to discover additional infrastructure. The ClickFix script in this case was used to download the SectopRAT malware, you can read more about the malware itself on my friend Chris’s blog here.
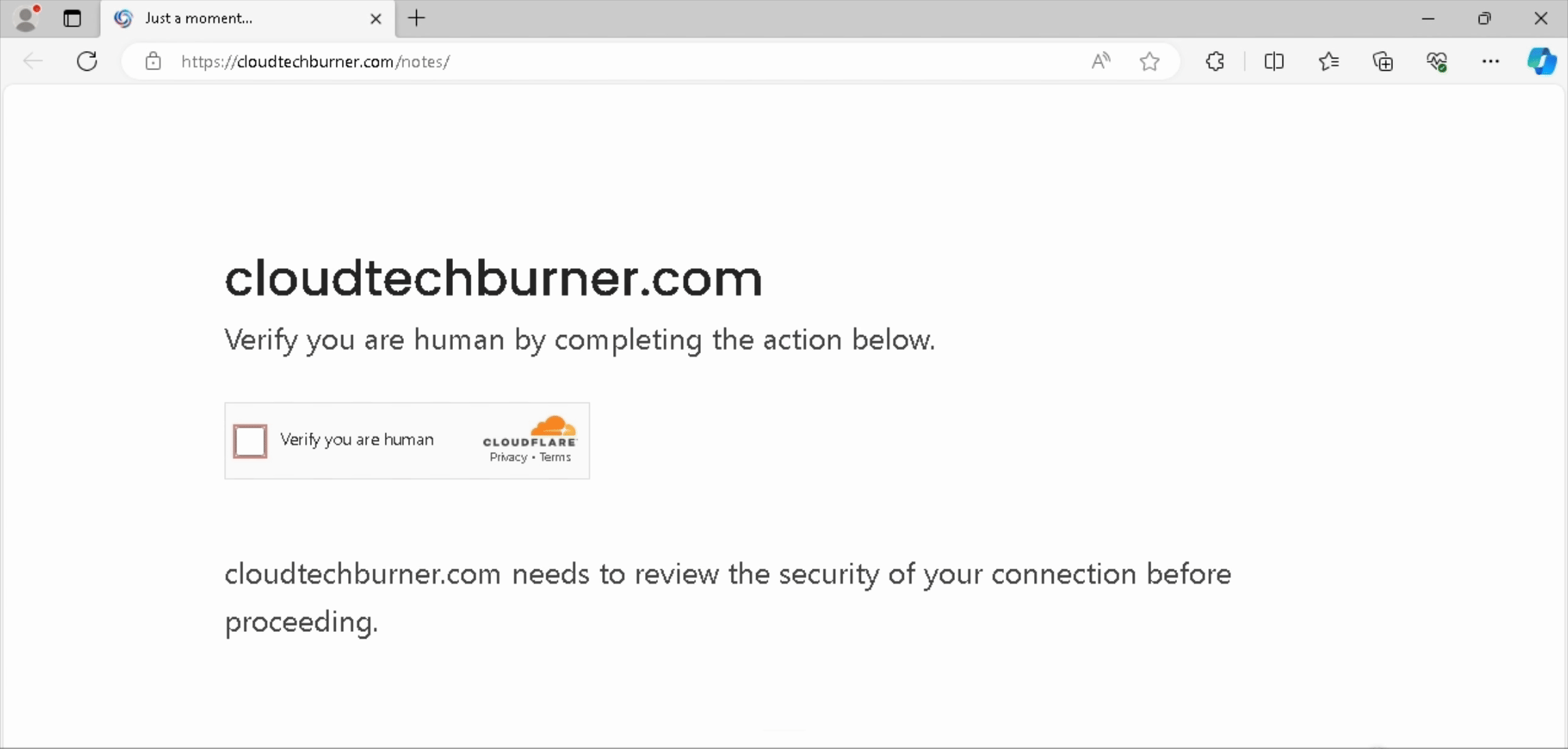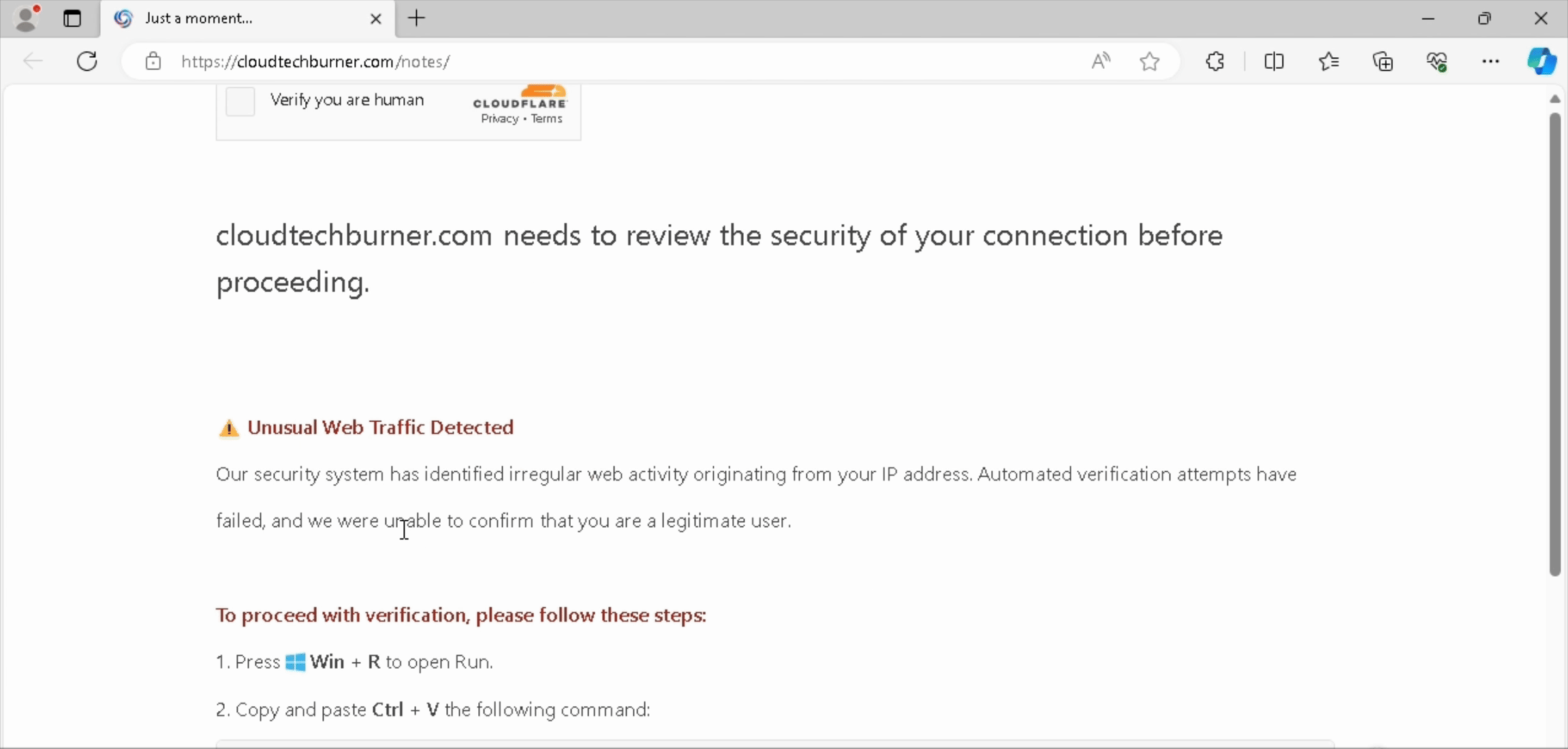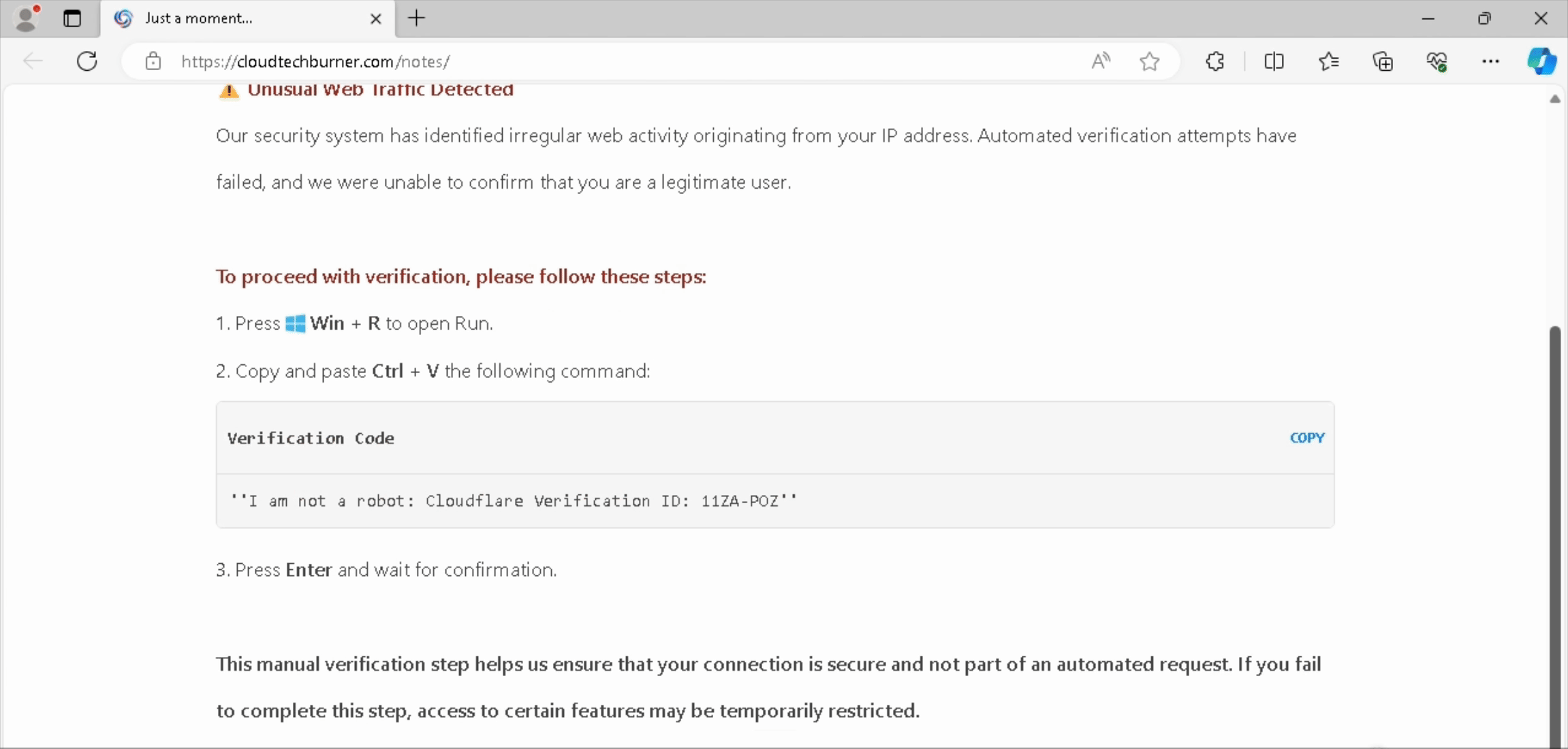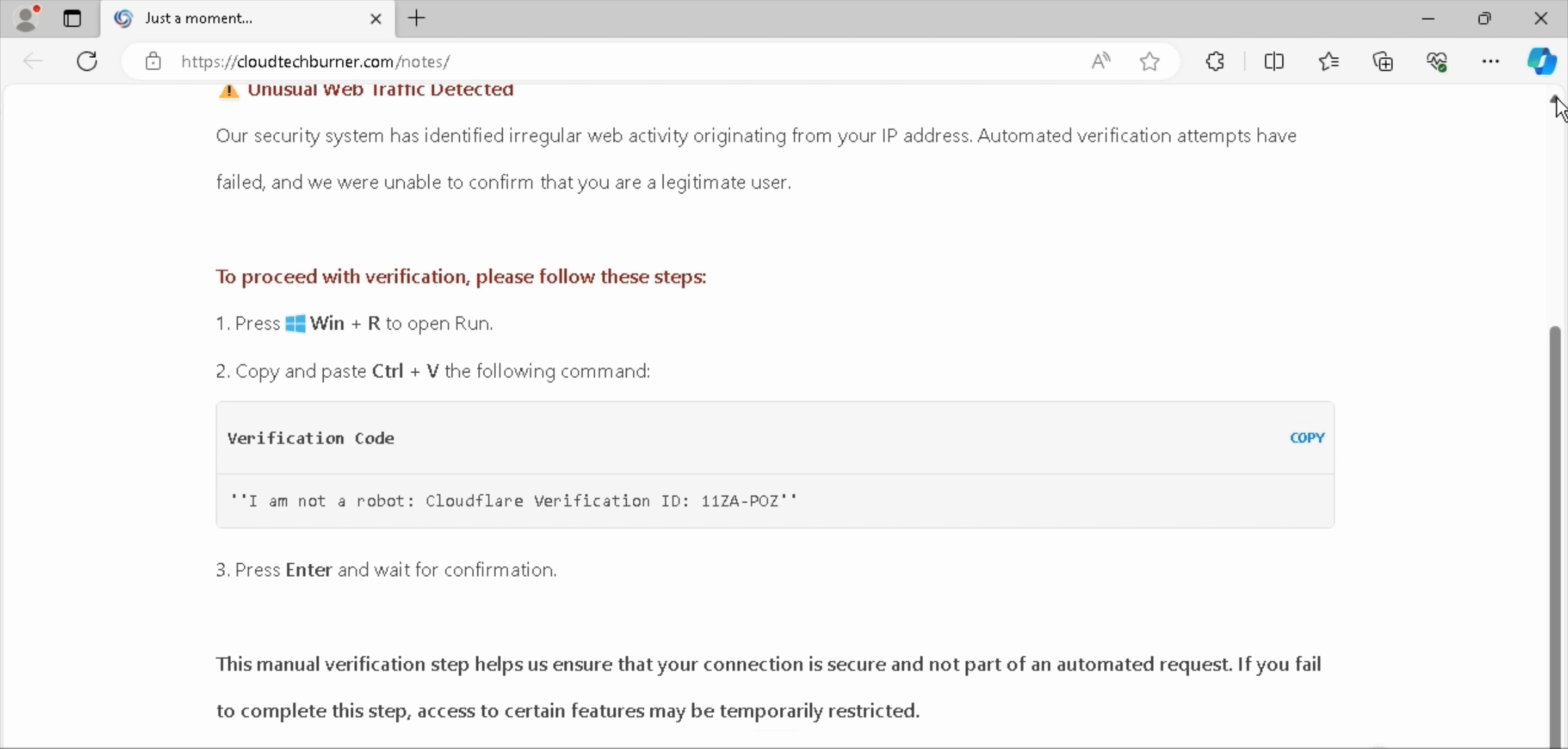
Our entry point for this campaign is cloudtechburner[.]com (recording below). When interacted with, the page fetches the ClickFix embed/payload from forfsakencoilddxga[.]com. We will now look at how forfsakencoilddxga[.]com can be latched onto to find other potential domains part of the ClickFix infrastructure for this campaign.
Looking up our first hop (forfsakencoilddxga[.]com) on VirusTotal, we can see that it has nameserver values for Cloudflare. Cloudflare in some cases issues the same set of nameservers to zones in an account. Therefore, we can try to use a stab in the dark technique to try find other domains that belong to the same Cloudflare account. Generally, a set of nameservers on its own is not enough, and you need other correlations to establish a high level of confidence to say that domains are operating behind the same Cloudflare account.
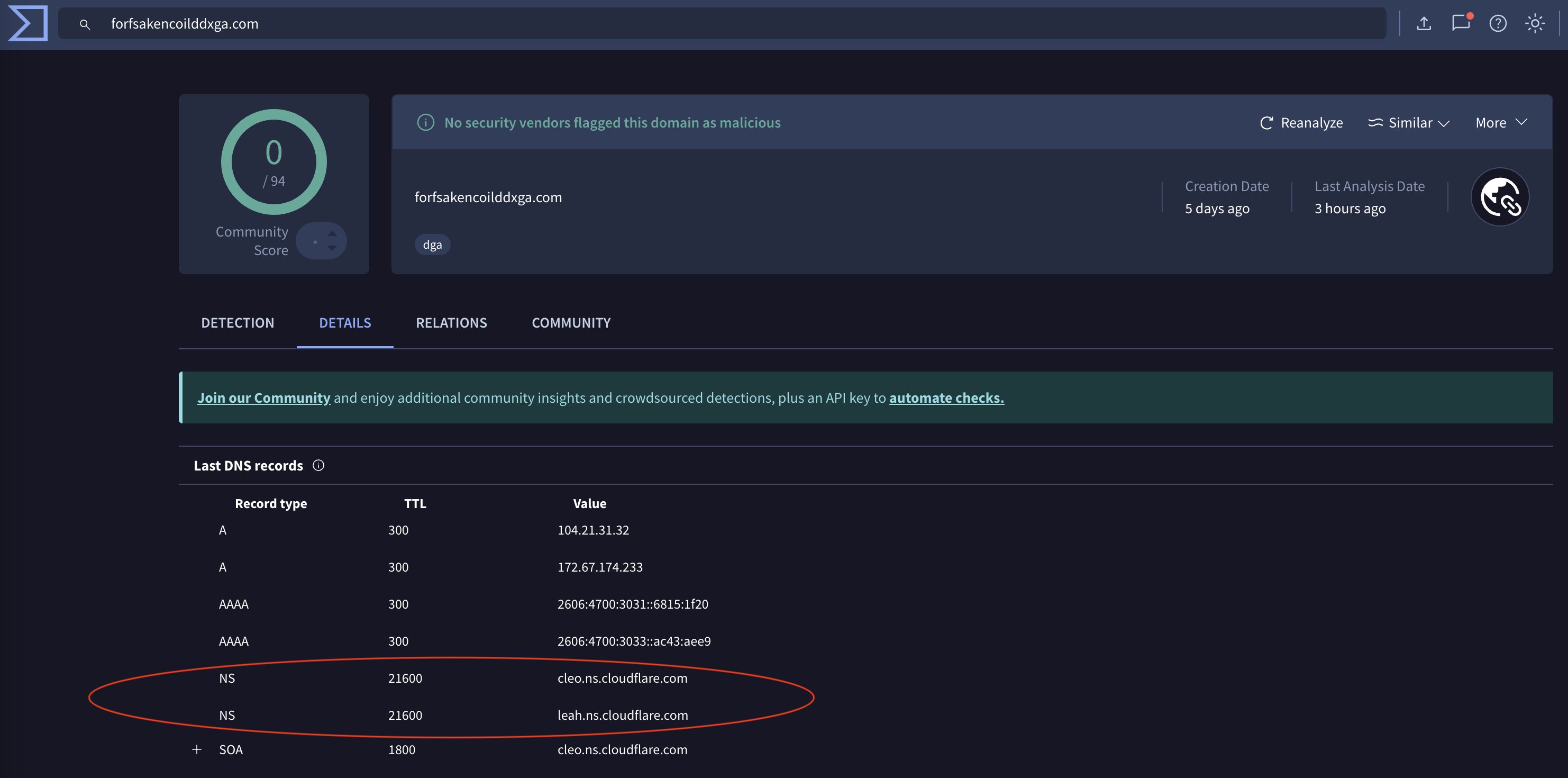
Using the following search term in VirusTotal entity:domain ns:cleo.ns.cloudflare.com ns:leah.ns.cloudflare.com, we are telling VirusTotal to give us all domains where they have nameserver values of cleo.ns.cloudflare.com and leah.ns.cloudflare.com. We get 95 unique domains (as shown in the screenshot below). The reason we see 95 domains is because Cloudflare has roughly 900 nameservers, resulting in ~810,000 unique combinations of nameserver records, which means that different accounts or zones can get the same set of nameserver records.
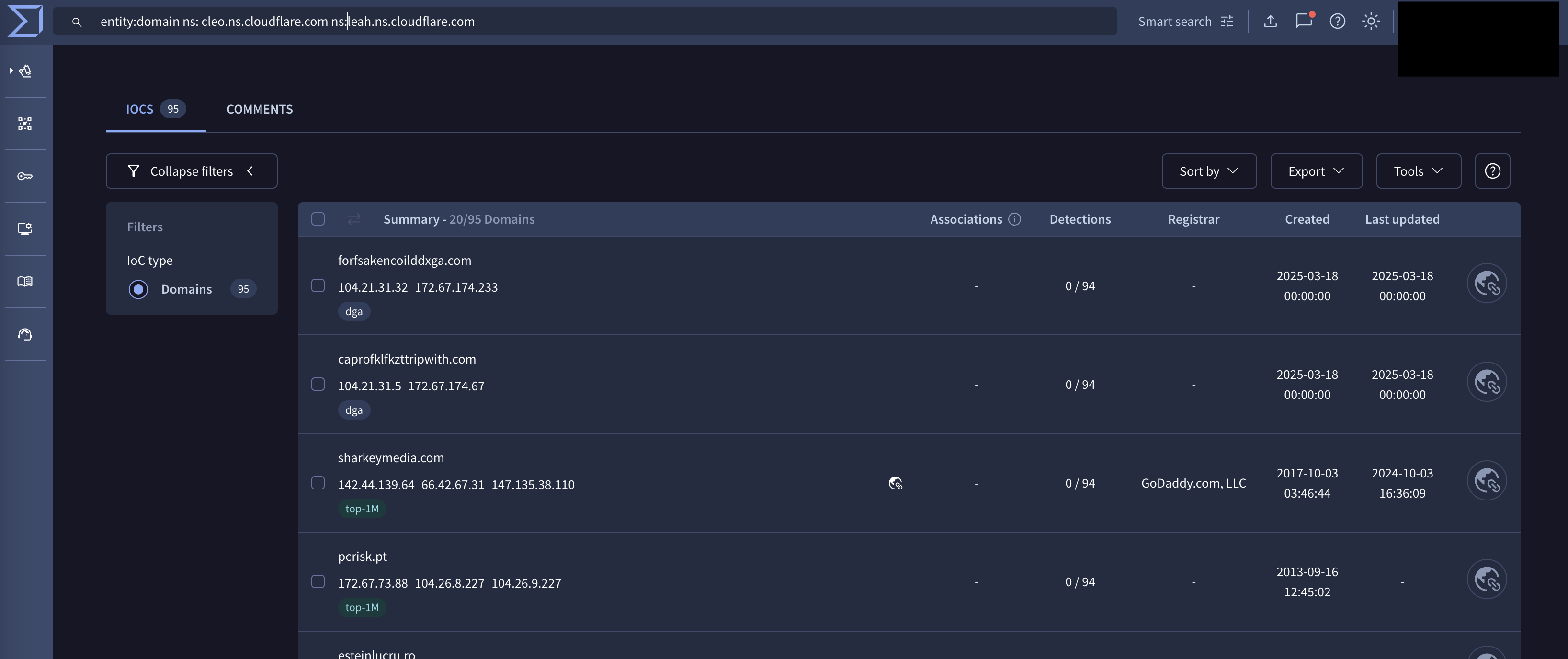
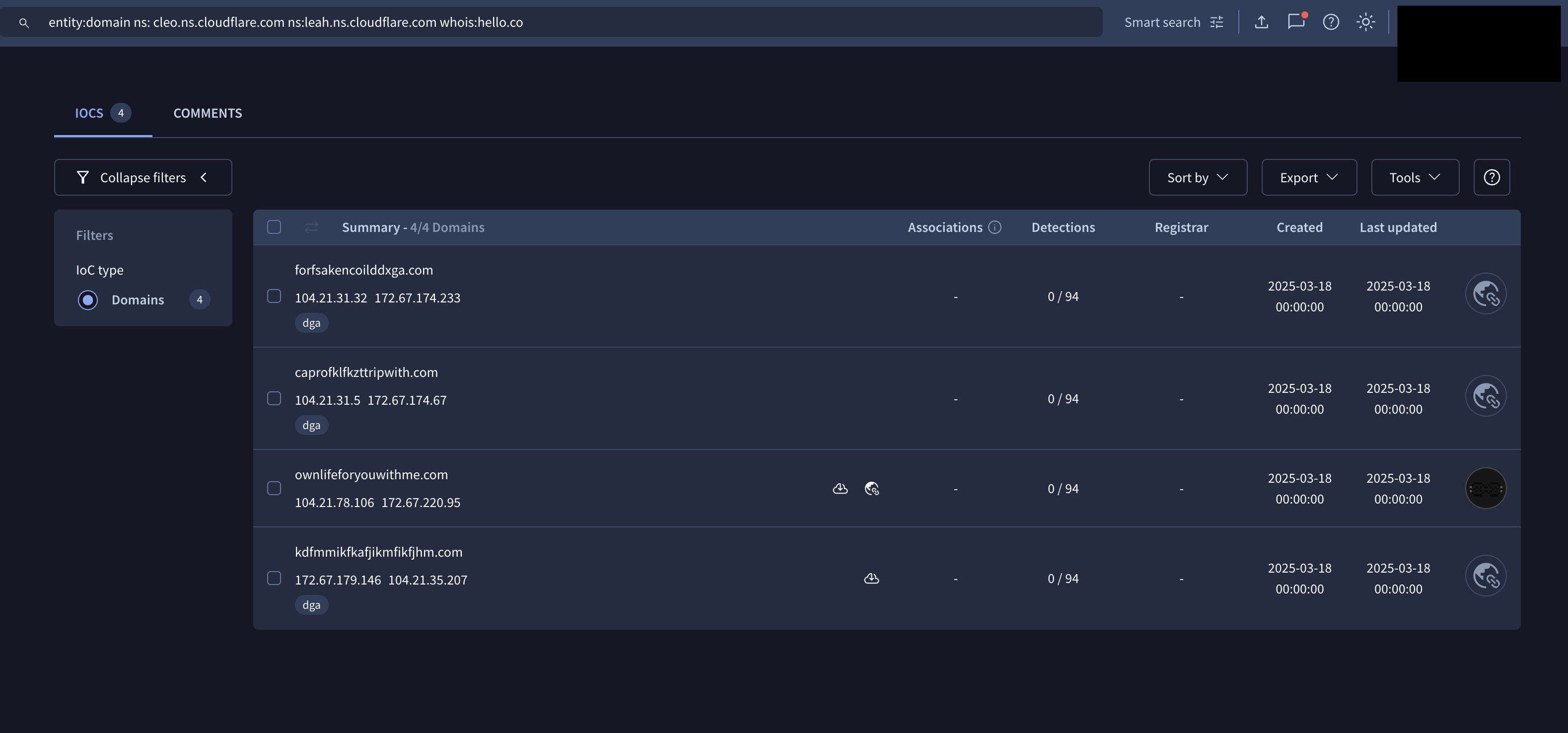
Interestingly, the very second domain we see in our search term is caprofklfkzttripwith[.]com. The domain was registered on the same date as our first hop, has the same registrar as our first hop (hello.co) and of course the same set of nameservers. For now, let’s call this a low to moderate probability of these domains being related and dig into it further. If we then expand our VirusTotal search to look for this specific registrar, we end up with the four domains below.
“Lets get this out onto a tray.” ~ Steve1989MREInfo
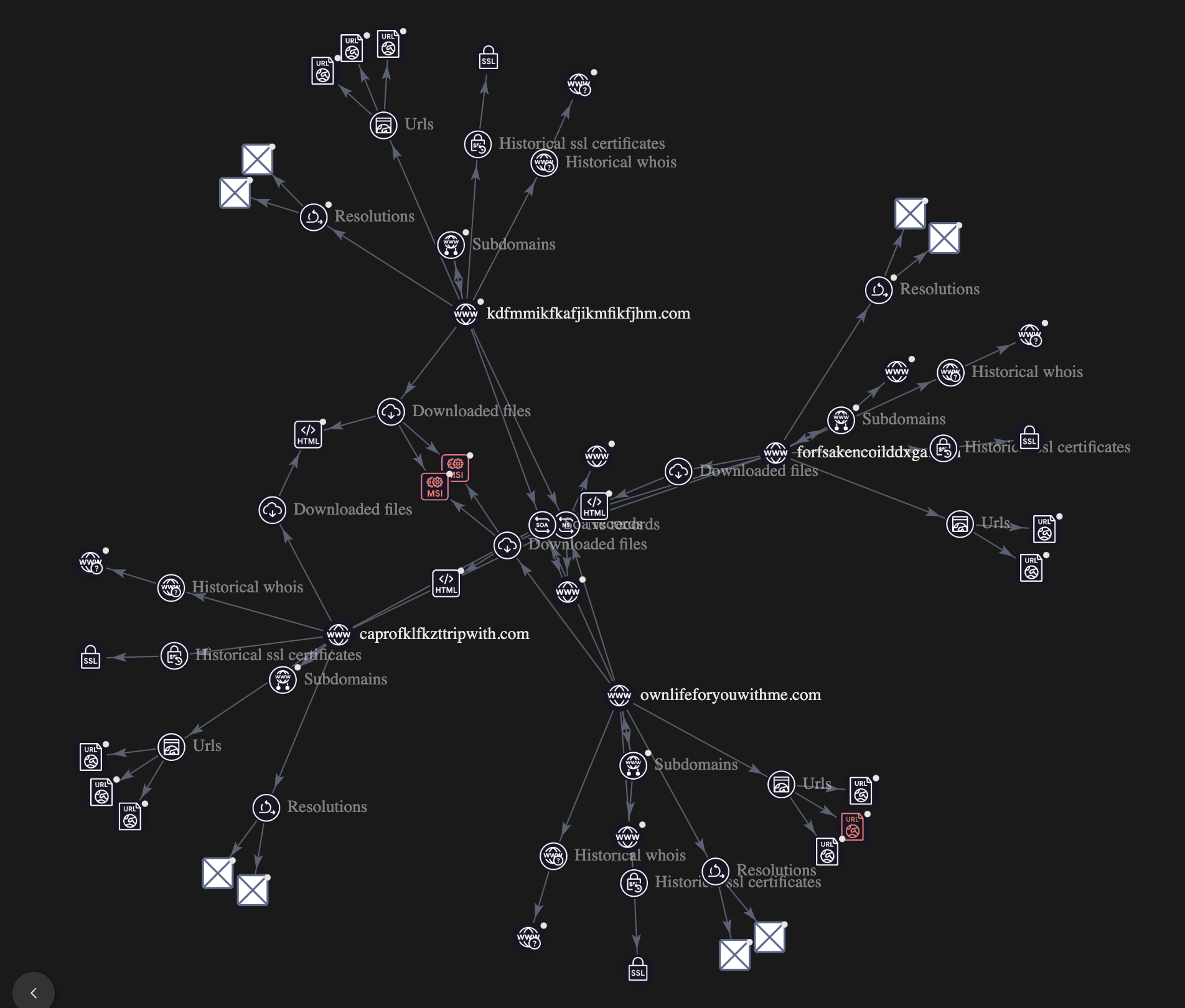
By inserting the four discovered domains into VirusTotal Graph, we start to build an image of what’s going on. Specifically, we start to see an overlap in malicious and downloaded file detections, domain registrar, domain creation date, DNS records and cross-domain file interactions.
Based on the information we discovered, we can establish that it’s highly probable that these four domains are under the same Cloudflare account, are controlled by the same entity and are part of the same campaign. To discover what each domain does and how it all ties together into the bigger picture, head on over to Chris’s blog!