Google Meet, Microsoft Teams and Zoom are all examples of common conferencing software used across large companies - companies that are large enough to be a juicy target for threat actors located in sanctioned countries. These actors, often just tech-savvy average joes, seek to get ahead by earning a US tech company salary. While their intent may not inherently be malicious, deception and fraud in getting the job can pose a reputational and legal risk to companies. This blog will cover how video conferencing software logs can be used to locate these threats.
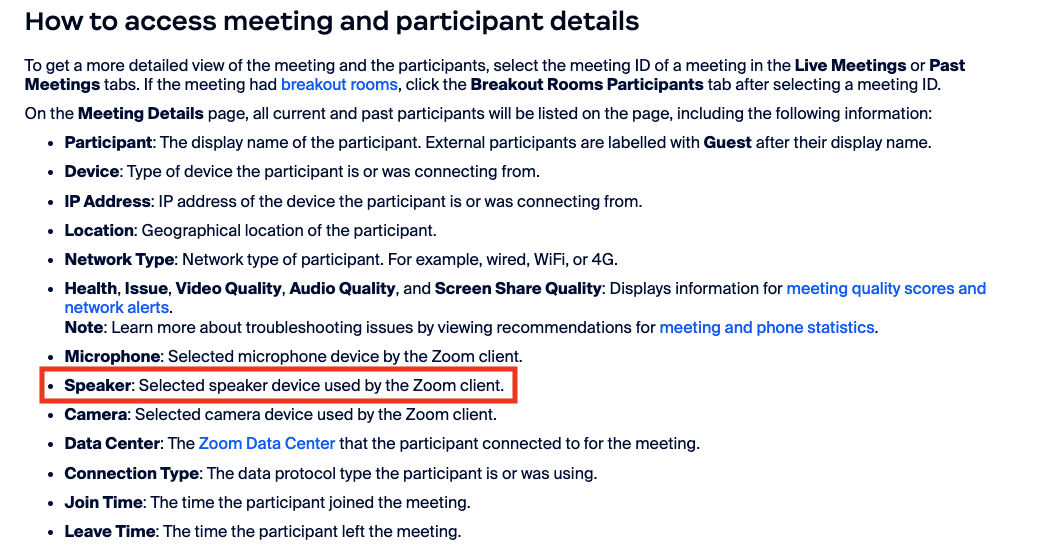
To get the information from your conferencing tool of choice, you likely need a level of privileged access, which will vary from platform to platform. Using Zoom as an example, this support page lists where the information we are after is located. Specifically, a field called Speaker is present in meeting details, as shown in the screenshot below.
Actors are often observed using a laptop-farm type setup, where they use a computer in their home country to connect to a laptop located in the country they are pretending to live in. If proper OPSEC is not observed by actors or they have a lapse in situational awareness (e.g., joining a Zoom meeting invite from origin device), these logs can help reveal their true location.
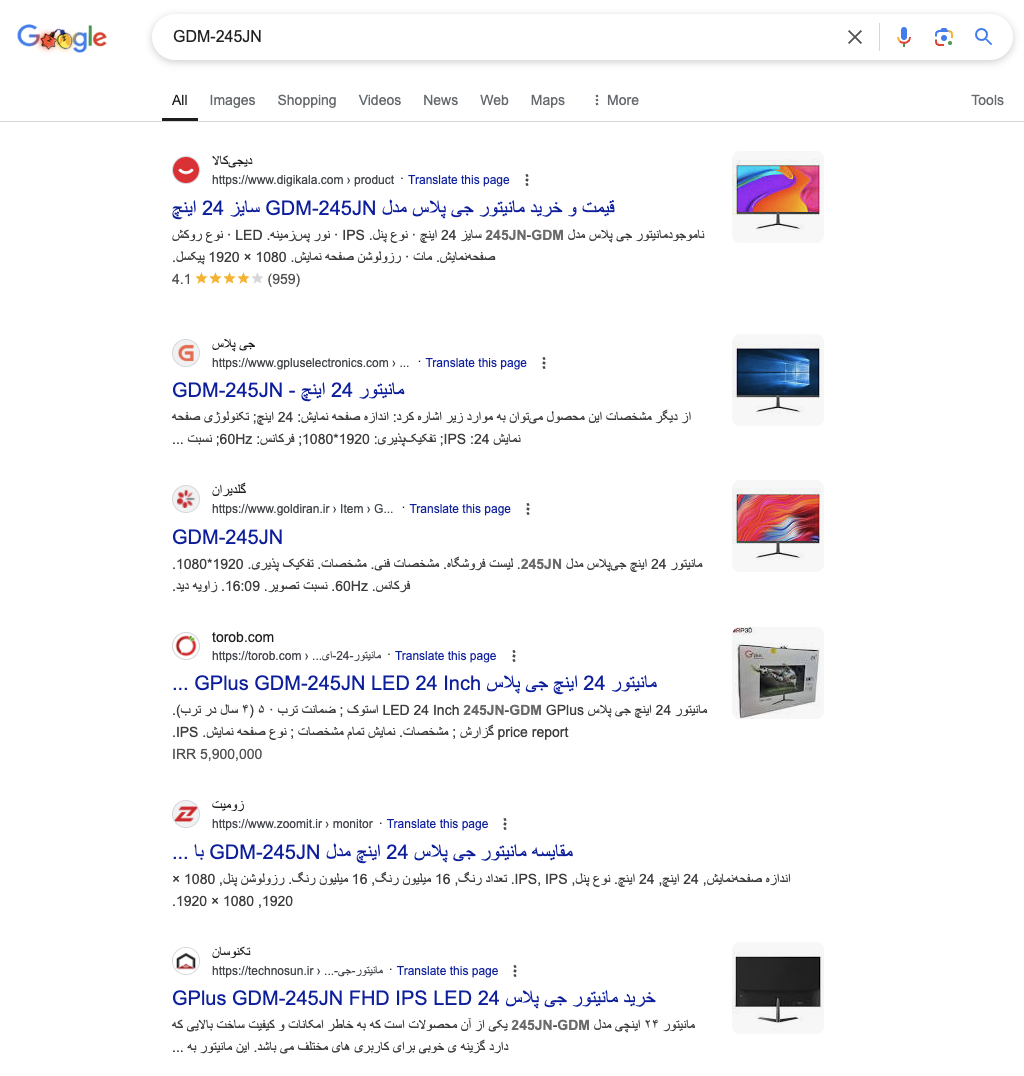
An example of a Speaker field log that would be interesting in such cases is GDM-245JN. When we research this model number, we see that various Iran-based sites are present in the results (screenshot below). The device in this case is a computer monitor, which has been selected as the audio output device by the actor. We can assess with high confidence that the device is primarily sold in Iran, and due to the trade embargos, it is unlikely for this specific model number to be naturally present in countries which many firms can operate from.
In an ideal world, a repository or data source of model-number-to-geographic-location relation would help in creating an automated detection. At the time of writing, I am not aware of a source that provides this reliably for speaker and/or monitor model numbers, and manual research is required to confirm whether this is a useful indicator for a given instance. The technique detailed in the blog above can be used to conduct Threat Hunts and/or to add enrichment to existing suspects.